The phrase “black projects” often conjures up shadowy images of government operations that seemingly defy the values of a transparent and open society.
But how exactly does the Department of Defense classify its systems? Delving into the “Special Access Program” (SAP), we aim to illuminate the clandestine procedures that safeguard the Pentagon’s most guarded secrets.
Dive into the clandestine world of the Special Access Program (SAP), where America’s most guarded secrets reside. This isn’t just any security protocol; it’s the epitome of top-tier confidentiality. Ready to uncover what lies beneath the shroud of SAP?
Understanding Special Access Programs

Introduction to Special Access Programs (SAPs)
Special Access Programs (SAPs) represent a critical element in the United States’ national security and defense framework. These programs are designed to control access, distribution, and protection of highly sensitive classified information beyond the standard security measures. SAPs are essential in ensuring that only a select group of individuals who have a demonstrated “need to know” can access this information. This stringent control is vital to protect national interests and prevent sensitive information from falling into the wrong hands.
History and Evolution of SAPs
The concept of Special Access Programs has evolved over time, reflecting the changing nature of threats and the growing complexity of national security needs. The origin of SAPs can be traced back to various legislative and executive actions, but they have significantly evolved to address modern-day security challenges. These programs have expanded in scope and sophistication, adapting to new technologies and shifting geopolitical landscapes. This evolution underscores the dynamic nature of national defense and the continuous need to protect sensitive information effectively.
Types of SAPs

Acquisition SAPs (AQ-SAPs)
Acquisition SAPs (AQ-SAPs) are primarily concerned with protecting the processes around the research, development, testing, modification, and evaluation or procurement of new defense systems. This category ensures that cutting-edge technology and critical defense systems remain secure from adversarial threats during their development and procurement stages.
Intelligence SAPs (IN-SAPs)
Intelligence SAPs (IN-SAPs), on the other hand, are focused on safeguarding sensitive intelligence operations. These may include covert operations, intelligence-gathering methodologies, and other activities that require an elevated level of confidentiality to be successful and secure. IN-SAPs play a pivotal role in the overall intelligence-gathering and analysis capabilities of the United States.
Operations and Support SAPs (OS-SAPs)
Operations and Support SAPs (OS-SAPs) are designed to protect the planning, execution, and support of sensitive military activities. These SAPs ensure that operations, which may be critical to national security, are conducted without unauthorized disclosure or interference. The protection offered by OS-SAPs extends to both planning stages and active operational phases.
Eligibility and Access
Gaining access to information within a SAP is governed by strict criteria. Individuals must not only have the appropriate security clearance but also a demonstrated “need to know.” This principle ensures that access to sensitive information is limited to those who require it for their specific duties, significantly reducing the risk of unintended disclosure or leaks.
Marking and Handling of SAP Information

SAP documents are subject to specialized marking to indicate their status clearly. This marking protocol involves the use of specific terms and codewords that denote the sensitivity and access requirements of the information. Such markings are essential for the proper handling, storage, and dissemination of SAP materials, ensuring that they are accessible only to authorized personnel.
In summary, Special Access Programs play an indispensable role in safeguarding national security by enforcing stringent controls over the access and distribution of critical information. Understanding the history, types, eligibility criteria, and handling procedures of SAPs is crucial for those involved in national defense and security operations.
For further details on the types of SAPs and their specific functions, you can visit Wikipedia and AcqNotes.
SAPs in Practice

SAPs in Government and Defense
Special Access Programs (SAPs) are integral to various government and defense agencies in the United States. Within these sectors, SAPs are employed to handle information and operations that are of utmost importance to national security. In the Department of Defense (DoD), for instance, SAPs play a pivotal role in protecting sensitive military technologies and operational plans. The importance of these programs extends to other branches of the government as well, where they safeguard crucial intelligence and counterintelligence information. The effectiveness of SAPs in these domains is a testament to their significance in upholding national security and defense protocols.
Security and Confidentiality
The core of SAPs lies in their ability to maintain the highest level of security and confidentiality. These programs employ a range of security measures, including stringent access controls, specialized communication channels, and advanced information protection technologies. The objective is to prevent unauthorized access and leakage of sensitive information, which could compromise national security. The robust security protocols surrounding SAPs underscore the gravity and sensitivity of the information they protect.
Legal and Ethical Considerations
The administration of SAPs is governed by a comprehensive legal framework, which ensures that these programs operate within the bounds of law and uphold ethical standards. This framework includes various executive orders, legislative acts, and departmental policies that dictate how SAPs are created, managed, and terminated. Adherence to these legal stipulations is crucial to ensure that SAPs fulfill their intended purpose without overstepping ethical boundaries or infringing on individual rights.
Contemporary Issues and Challenges
In today’s rapidly changing global landscape, SAPs face a range of contemporary issues and challenges. These include adapting to new technologies, countering evolving threats, and managing the balance between security and transparency. As threats become more sophisticated, SAPs must continually evolve to counter them effectively while maintaining the trust and confidence of the public and the personnel who depend on their integrity.
Conclusion
Special Access Programs are a cornerstone of the United States’ national security apparatus. Their role in protecting sensitive information and operations is invaluable. As the world continues to change, the importance of SAPs in adapting to new challenges and threats remains paramount. Their continued evolution and adherence to legal and ethical standards will be critical in safeguarding national interests in the years to come.
For more detailed insights into the role of SAPs in government and defense and their legal and ethical considerations, you can explore resources at DOE Directives, Guidance, Delegations, and ClearanceJobs Support.
Special Access Program (SAP) FAQs

What is a Special Access Program (SAP)?
A Special Access Program (SAP) is a security protocol within the U.S. government that provides heightened protection for highly classified information. It controls access and distribution, ensuring that only a minimal number of cleared employees, with a strictly need-to-know basis, have access to this information. SAPs are utilized for protecting sensitive classified information beyond the regular classified information requirements.
Who is eligible for access to SAP?
Eligibility for access to a SAP is highly restricted and is based on stringent need-to-know criteria. Generally, those with access to SAP information hold high-level security clearances, such as SECRET or TOP SECRET. However, holding such clearances alone does not automatically grant access to SAP information. Interim access eligibility for SAPs is granted under very limited circumstances.
What are the types of SAPs?
SAPs are classified into two types: acknowledged and unacknowledged. Acknowledged SAPs may have their existence publicly disclosed, but their details remain classified. Unacknowledged SAPs, also known as USAPs, are disclosed only to authorized individuals, including specific members of the United States Congress. There are also waived SAPs, which are a subset of unacknowledged SAPs in the Department of Defense, exempt from most reporting requirements.
What are the categories of SAPs within the Department of Defense?
There are three main categories of SAPs within the Department of Defense:
- Acquisition SAPs (AQ-SAPs) focus on the protection of research, development, and procurement of new systems.
- Intelligence SAPs (IN-SAPs) protect sensitive intelligence operations.
- Operations and Support SAPs (OS-SAPs) safeguard sensitive military activities and operations.
How are SAP documents marked?
SAP documents require specific markings to indicate their status. These include the words “SPECIAL ACCESS REQUIRED” followed by the program nickname or codeword. This marking is placed on the document’s banner line. Additional markings like SAR (Special Access Required) and the program’s abbreviation are also used. The marking system ensures proper identification and handling of these sensitive documents.
What additional controls are imposed by SAPs?
SAPs impose additional controls governing access to classified information beyond normal management and safeguarding practices. These controls may include access approval, adjudication or investigative requirements, special designation of officials authorized to determine a need-to-know or special lists of persons determined to have a need-to-know. These measures are in place to ensure the highest level of security and confidentiality for the classified information handled within a SAP.
These FAQs provide a basic understanding of the Special Access Program, highlighting its significance, types, categories, and the stringent measures in place for the protection of sensitive information.
How Does the U.S. government protect and restrict access to highly classified information?
Ensuring the safety of and restricting access to highly sensitive information is a paramount responsibility of the U.S. government. This is achieved through an intricate system of compartmentalization known as “Special Access Programs” or SAPs.
SAPs are not arbitrary designations; they are a comprehensive set of security measures designed to ensure that only those explicitly authorized and truly need to know are granted access to the most sensitive information.
This stringent control is crucial, particularly in sectors such as the Department of Defense, where protecting classified intelligence can have significant ramifications for national security. Let’s delve deeper into the mechanisms and intricacies of the Department of Defense’s classified system.

How is National Security Information classified? And how is the Department of Defense’s system classified?
Here’s a brief overview of how these systems work:
National Security Information Classification:
- Executive Order 13526: This is the primary guiding document for the classification of national security information. It sets out criteria, levels, and procedures for classifying, declassifying, and safeguarding sensitive information.
- Classification Levels: There are three primary levels of classification based on the sensitivity of the information and the potential harm that could result from its unauthorized disclosure:
- Top Secret: Unauthorized disclosure could reasonably be expected to cause exceptionally grave damage to national security.
- Secret: Unauthorized disclosure could reasonably be expected to cause serious damage to national security.
- Confidential: Unauthorized disclosure could reasonably be expected to cause damage to national security.
- Determining Classification: Original classification authorities (OCAs) are officials designated by the President or agency heads. They are authorized to classify information at the appropriate level. Classification is not indefinite; a declassification date or event is usually set.
- Need-to-Know Principle: Even if someone has clearance for a certain classification level, they are only given access to the information if they have a legitimate need to know it for their duties.
Department of Defense’s Classification System:
- Alignment with National Standards: The DoD’s classification system largely aligns with the national classification system. The DoD follows the guidelines and procedures outlined in Executive Order 13526.
- Special Access Programs (SAPs): Beyond the standard classification levels, the DoD has SAPs to restrict further access to information that requires an additional layer of protection. SAPs compartmentalize information, ensuring that only those with specific authorization can access it, even if they have a high-level security clearance.
- DoD Manual 5200.01: This manual provides the DoD’s comprehensive guidance on its classification system, detailing the procedures and responsibilities for classifying, safeguarding, and declassifying defense information.
- Training & Oversight: Personnel within the DoD undergo regular training on handling classified information. Additionally, oversight mechanisms ensure that classified information is correctly marked, stored, transmitted, and eventually declassified or destroyed when no longer needed.
In essence, the classification systems are established to strike a balance between transparency and the protection of information critical to U.S. national security and defense.
“Black Programs”
Moreover, according to the Center for Development of Security Excellence’s (CDSE) Special Access Programs Training Course, from the 1970s to 1980s, SAPs—referenced even within the government as “black programs”—were virtually exclusively restricted to safeguarding DoD acquisition programs.

“Special Access Programs,” acronym—”SAP.”
By the mid-1990s, those secret workshops shed the “black program” moniker, opting to go by the more contemporarily well-known SAP or “Special Access Program.”
In addition to the more dexterously smooth title, intelligence, operations, and support programs were added to the SAP, establishing the Special Access Program regime we’ve come to know today.
When viewing the term “special access program,” people envision one of the three categories within the Department of Defense.
- Acquisition SAPs: Programs include research, evaluation, development, testing, modification, or procurement of new technologies. Moreover, according to the CDSE, Acquisition SAPs make up 75-80% of all DoD SAPs.
- Intelligence SAPs: – The planning and execution of sensitive, intelligence or counter-intelligence operations.
- Operations and Support SAPs: – Planning, implementation, and support of sensitive military enterprises.
Furthermore, separate from an objective category, all SAPs (special access programs) fall under one of two protection levels:
- “Acknowledged” – Those are programs whose existence and purpose can be openly recognized. Only intimate details, like technologies, materials, or techniques, are kept secret. Funding for Acknowledged SAPs is mainly unclassified and can be readily seen in the government’s fiscal budget.
- “Unacknowledged”- This is the shy sibling of the SAP family. When an SAP is designated as “unacknowledged,” not only is a program’s purpose carefully guarded, as the name implies, its mere existence may be denied to everyone but a few who aren’t a part of the program. It should come as no shock; the funding for unacknowledged “special access programs” is either classified or purposely hidden within the Federal budget.

Serving on the secrecy mosaic’s front lines is the “Special Access Program Central Offices” (SAPCO). It thrives on compartmentalization, and by “central,” the DoD means there are three different types of SAP Central Offices.
- SAPCO or Component-Level SAP Central Office: They can be found within each branch of the U.S. military, the Joint Chiefs of Staff, the Defense Advanced Research Projects Agency (DARPA), and the MDA, or Missile Defense Agency. The Component-Level SAPCOs are responsible for starting the prospective process for accessing an SAP. Once a Special Access Program has been installed, a Component-Level SAP Central Office works as the hands-on manager for the Special Access Program that falls under their scope.
- OSD SAPCO or Office of the Secretary of Defense-Level SAP Central Office: – It was installed to assist the Deputy Secretary of Defense. Furthermore, the Secretary of Defense-Level Central Office Office serves as the overseeing authority for all SAPs.
- DOD SAPCO or Department of Defense SAP Central Office: – Working to help streamline this entire fragmented, the Department of Defense SAP Central Office functions as an ambassador by communicating and advising the executive branch and Congress agencies on all matters relating to SAPs.
The Special Access Program administration structure
Spearheading the Special Access Program governance or administrative structure is the SAPOC or Oversight Committee. It’s made up of a who’s who of Pentagon Under Secretaries, Assistant Directors, and Vice Chiefs.
The Oversight Committee’s main role is to assist and advise the Secretary and Deputy Secretary of Defense in the governance, management, and oversight of all Department of Defense (DoD) Special Access Programs.
Ensuring that the limitation of secrecy to only a picked few isn’t a decision made in a vacuum, assisting the Special Access Program Oversight Committee is:
- Senior Review Group (SRG): – The main working-level body that governs the Special Access Program oversight process.
- SAP Senior Working Group (SWG): – Gives recommendations to the Senior Review Group and works as a senior program protection forum coordinating, deconflicting, and integrating special programs.

Guarding Special Access Programs
In the span of SAP controls, OUSDI or the Office for the Under Secretary of Defense for Intelligence SAP Control Office fills the important role of monitoring and investigating counter-intelligence matters, security violations, or infractions of all Department of Defences SAPS.
Supporting OSDi’s Central SAP Office in this work is the Office of the Director of National Intelligence and the 17 individual agencies that make up the United States intelligence community.
Reinforcing this mighty SAP Central Office, the U.S. Defense Security Service (DSS) provides operational assistance and security oversight for all DoD SAPs.
But the first line of defense in guarding the integrity of SAP secrecy starts with who is granted access to a secret program.
So, regardless of whether a person is a federal-civilian employee, in the military, or a private contractor, many requirements must be met before working within an SAP.
Once inside an SAP, there are still many vital roles that help ensure each special access program’s secure integrity. Some of those are:
- The Government Program Manager (GPM), and their private industry equivalent, the Contractor Program Manager (CPM): – The person who oversees all aspects of a specific program.
- Program Security Officer: – The person responsible for all aspects of security in the program. Every SAP has a PSO. However, large or complex SAPS can additionally have extra Government SAP security officers or contractor program security officers to support the Program Security Officer.
Additionally, protecting who knows what, an SAP’s overarching scope and purpose can fall under one program “umbrella.”
Nevertheless, multiple compartments can further break down into separate sub-compartments, and numerous projects can all emerge under a single SAP umbrella.
So, it’s completely possible for a compartment, sub-compartment, or project not to have access to or be aware of the work that’s going on in other sections of the same SAP.
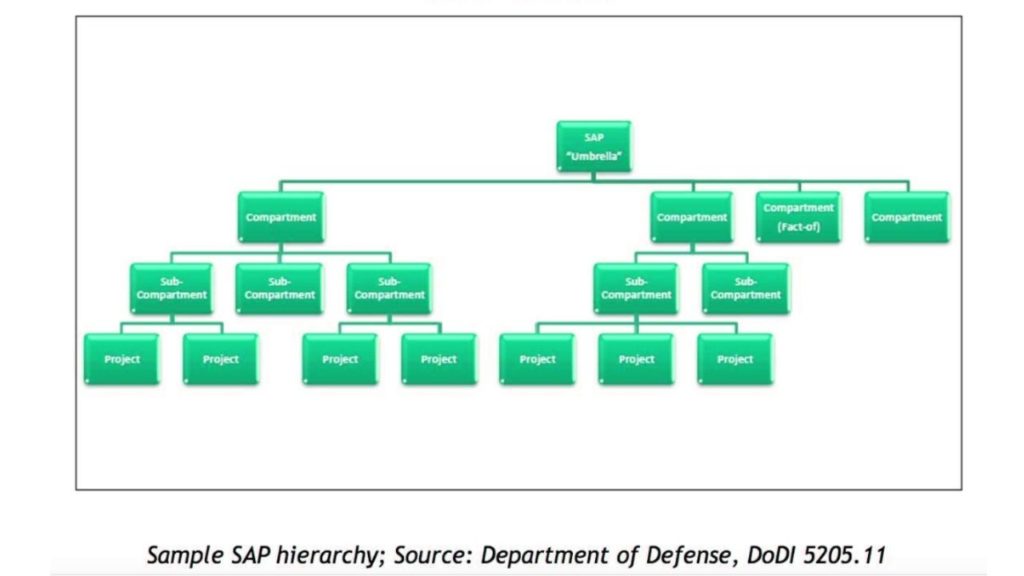
Oversight Of Special Access Programs
All SAP or Special Access Programs are subject to federal and defense acquisition regulations.
Therefore, all Special Access Programs can be audited and inspected by many oversight entities, including the DoD Inspector General or the Government Accountability Office.
Equivalently, oversight of SAPs isn’t merely left to agency directives and policies. Instead, it’s a matter of federal law.
All active acknowledged and non-waived unacknowledged SAPs must submit reports to the House and Senate Authorization, Appropriations, and Intelligence Committees yearly by federal statute.
Those yearly reports give committee members an estimated total budget request for the upcoming fiscal year, a short description of the program, including the number of persons involved, current issues, the status of significant milestones, and the program’s actual cost for each previous fiscal year.
Each member not assigned to one of the defense or intelligence committees may be granted access to non-waived special access programs. They receive permission from the ranking and minority members from each of the respective committees and with the Secretary or Deputy Secretary of Defense’s approval.
So, when it comes to Special Access Programs (SAPs), like virtually all government operations, they are mostly cumbersome bureaucratic affairs. However, now you hopefully know how the underlying secrecy processes work.
For a deeper dive into the intricacies of the Department of Defense’s perspective on unidentified aerial phenomena, consider reading our detailed analysis on ‘Deciphering the Department of Defense’s Stance on UAPs.’ This article offers an enlightening exploration of the DoD’s approach and understanding of these mysterious occurrences.
